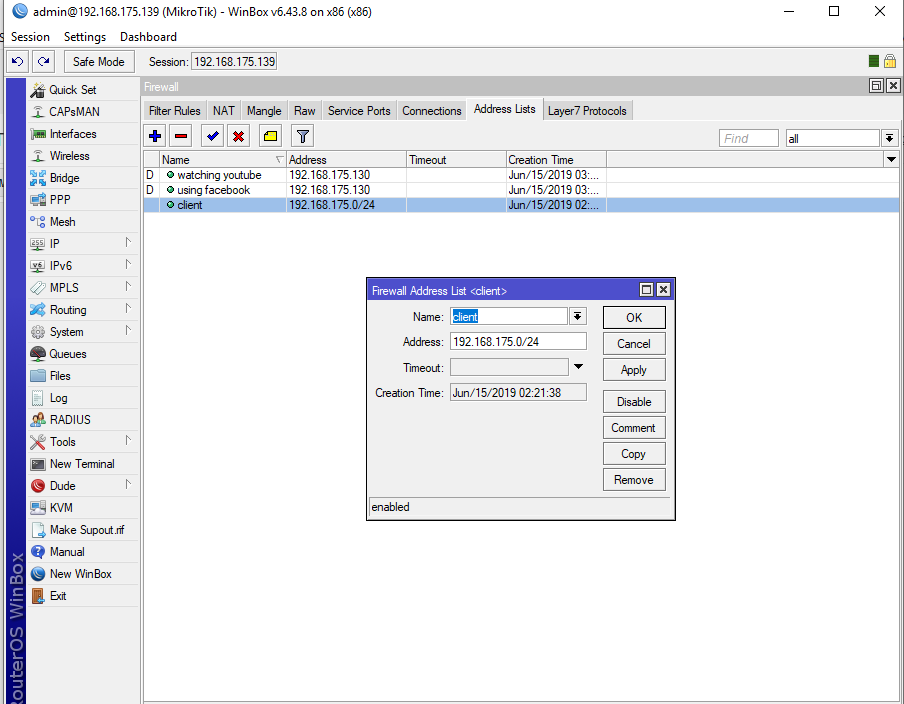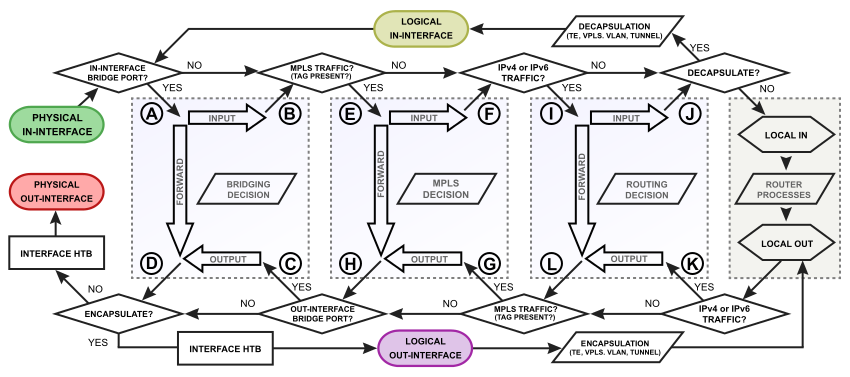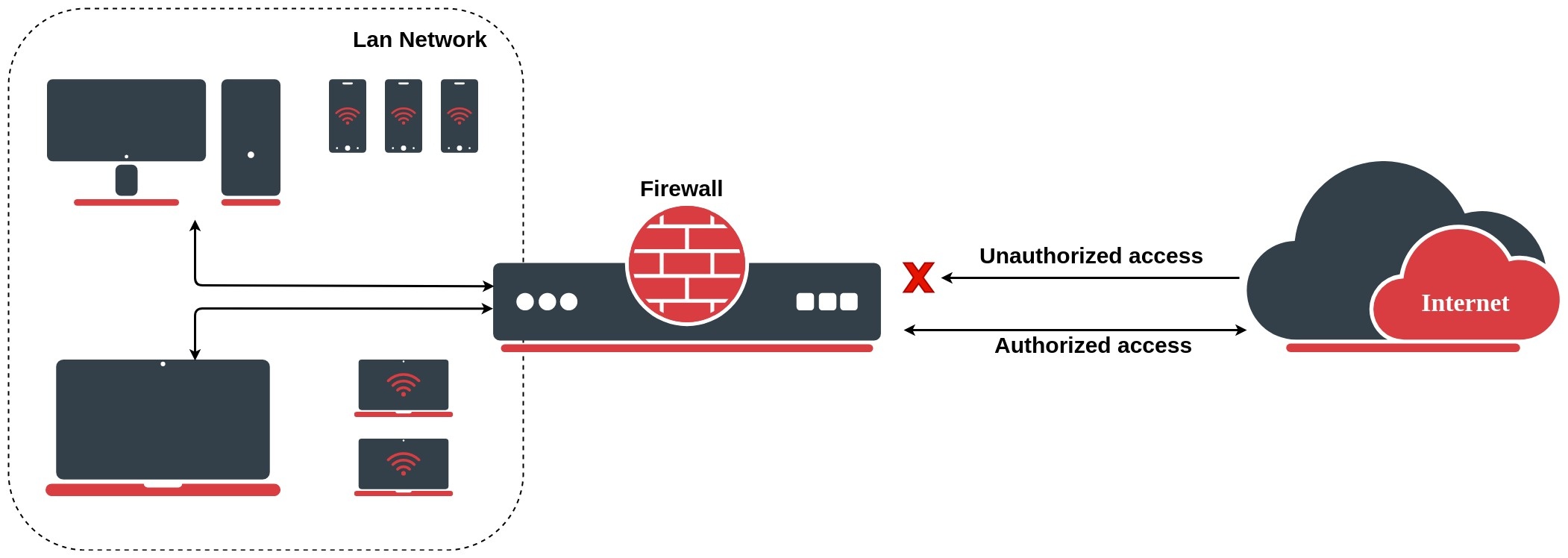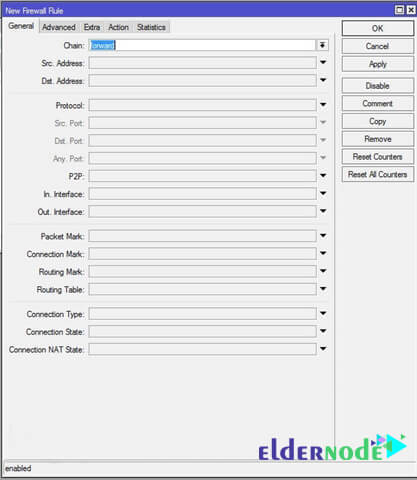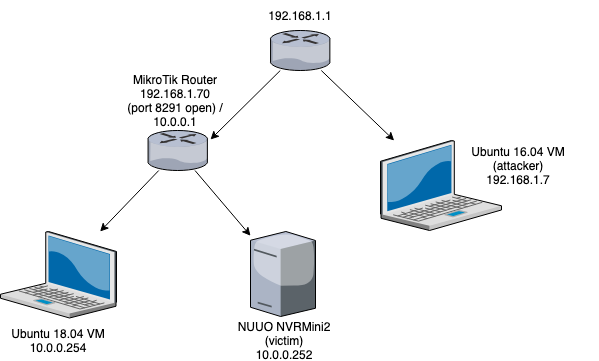
MikroTik Firewall & NAT Bypass. Exploitation from WAN to LAN | by Jacob Baines | Tenable TechBlog | Medium

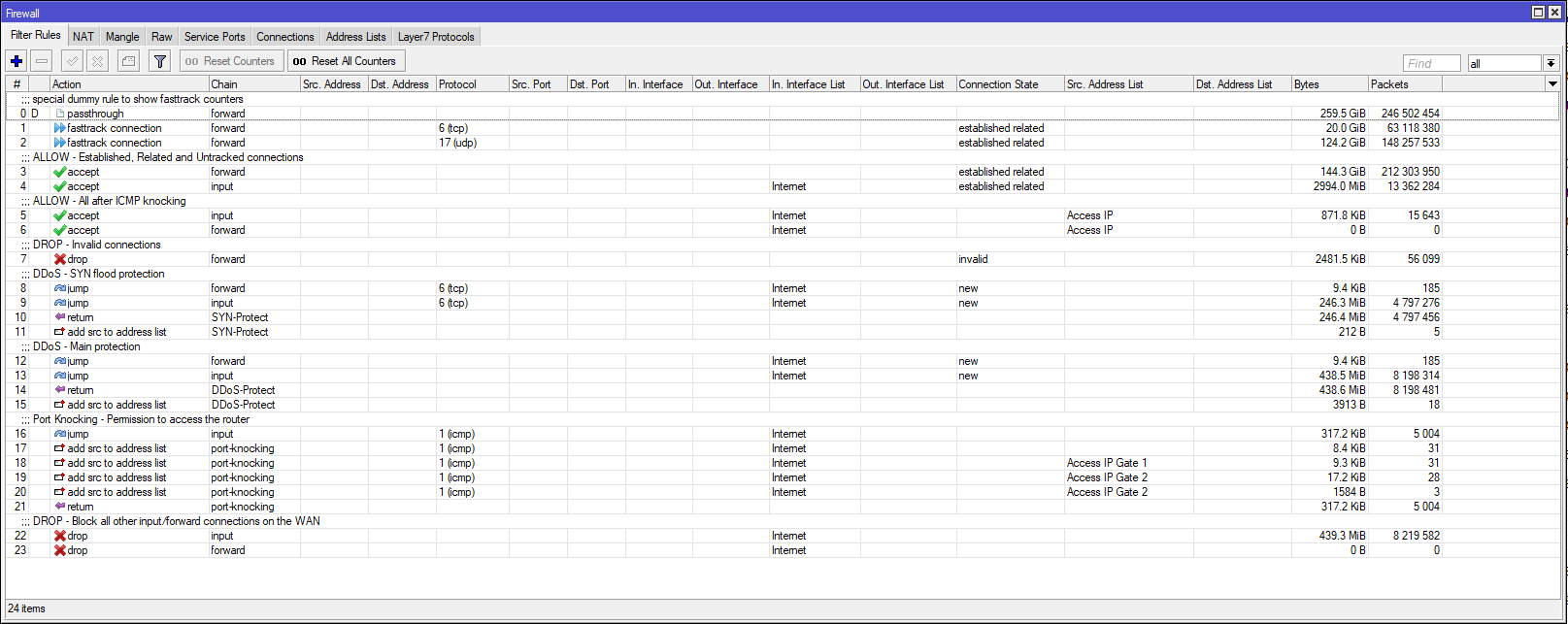
MikroTik CVE-2019-3924 Firewall & NAT Bypass: Exploitation from WAN to LAN - Lawrence Technology Services

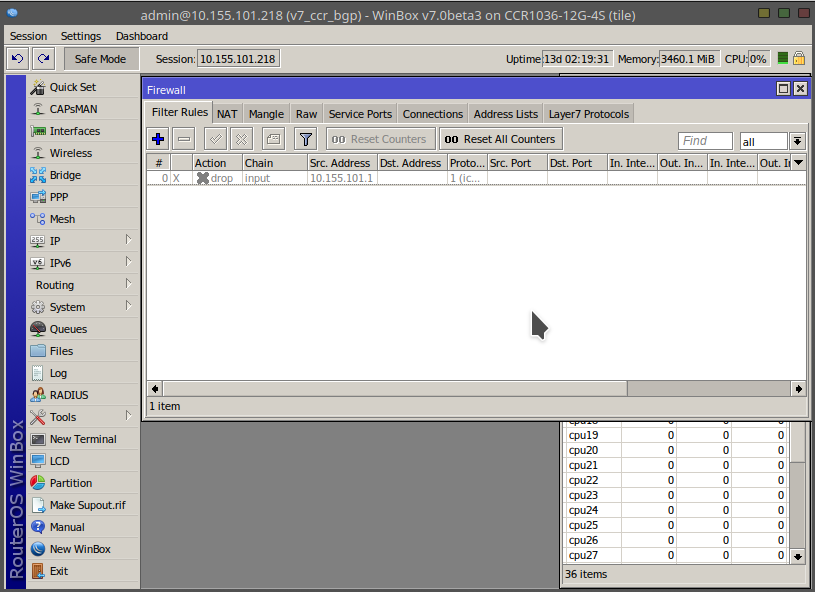
MikroTik Firewall & NAT Bypass. Exploitation from WAN to LAN | by Jacob Baines | Tenable TechBlog | Medium

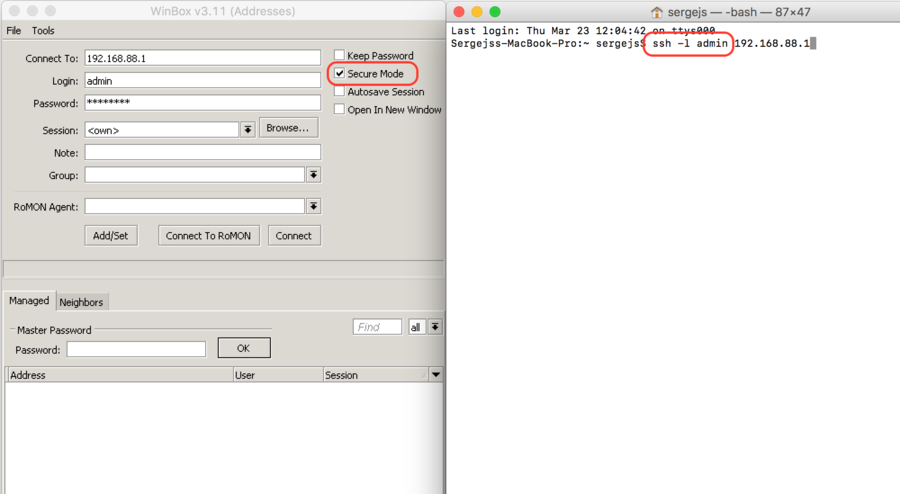
MikroTik Firewall & NAT Bypass. Exploitation from WAN to LAN | by Jacob Baines | Tenable TechBlog | Medium